Congratulations – your software product is live! It’s a milestone worth celebrating. At this stage, business owners typically fall into three different categories of thought:
Reality often disrupts these plans. Maintaining a live application and keeping users satisfied can require as much effort as the initial development. In this article, we’ll explore post-launch challenges you might face and how to tackle them with confidence.
Bugs on Production
Bugs on production are unavoidable, but you can mitigate the worst of them with solid quality assurance (QA) processes. A mix of manual and automated testing can minimize errors and ensure smooth, speedy releases. Well-written test cases that are continuously revised and updated help ensure core functionality performs optimally and the worst bugs are caught early.
Great QA is an investment and can even rival development costs. However, cutting corners on QA can lead to costly disruptions down the road, such as rollbacks, user dissatisfaction, and even downtime. While it’s impossible to catch every bug, solid QA processes reduce these risks significantly.
Performance Issues
If there’s one thing you can count on, it’s that users are unpredictable. Even if your team performed load testing and stress testing before launch, these tests were based on assumptions of typical user behavior. Real users can, and often will, behave differently than expected.
For example, say you stress-tested performance with the expectation that users will log on at various times throughout the workday. However, once you launch, you discover that the majority of your users use your system at the start of the day, simultaneously, and it is less responsive during the “warm up” period. Or, some users obsess over the new reporting features, which results in a less efficient database cache.
Alternatively, consider a social network for peers and relatives to connect and exchange texts and photos. Users tend to have 100-1000 friends, and it works smoothly… up until Taylor Swift creates an account and suddenly has 1,000,000 friends or followers. This imbalance could break the system design.
Real-world usage often defies assumptions. You cannot plan for every scenario, but rather, you need to be ready to adapt on the fly. This requires regular performance monitoring and a scalable infrastructure.
Security Vulnerabilities
Even well-written, secure code can be exposed to vulnerabilities, often through third-party libraries, frameworks, or even hardware. Recent threats like Log4Shell, Meltdown, and the Terrapin Attack provide reminders that staying vigilant isn’t optional – it’s essential.
Mitigating these risks requires more than simply patching known vulnerabilities. It requires consistent, proactive monitoring, timely updates, and staying informed about emerging threads. Security isn’t a one-time effort, it’s an ongoing commitment.
Outdated Tech Stacks and Frameworks
Technology evolves rapidly. Frameworks and platforms -like Angular, Node.js, or .NET- are constantly updated to improve security and performance. These platforms and frameworks are often supported by large corporations, such as Apple or Microsoft, or large groups of open-source contributors. These constant updates require a massive investment of time, resources, and money. The constant need to evolve limits the improvements and security patches to the most recent versions.
Even if your application launched recently, a migration may already be necessary. This can make staying current feel like chasing a moving target. The key is to use stable or long-term support (LTS) versions when possible and plan for regular updates to avoid falling behind.
PostgreSQL
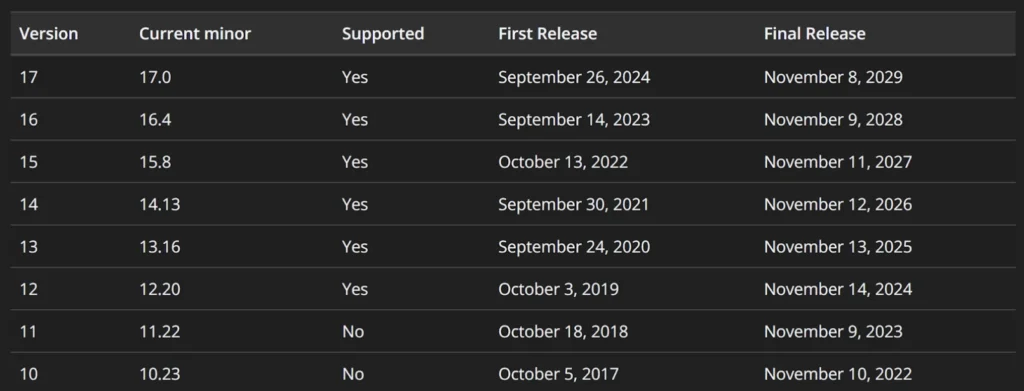 Node.js
Node.js
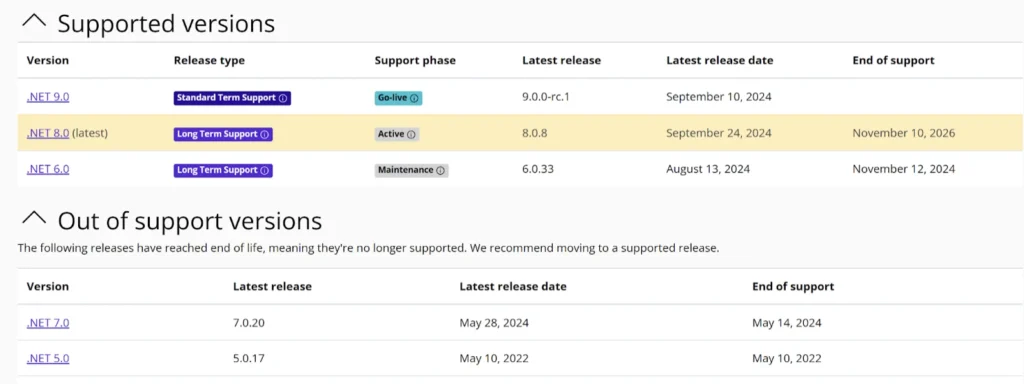
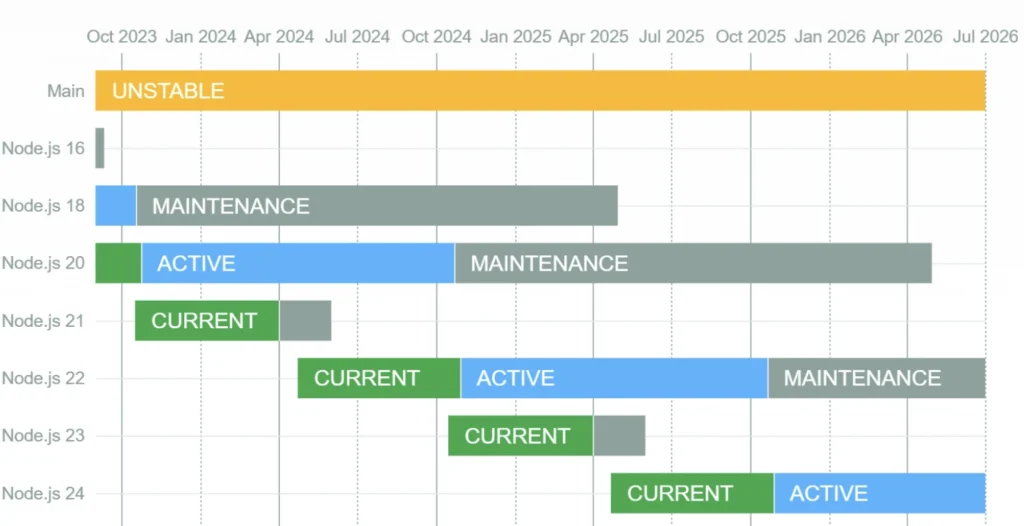 .NET
.NET
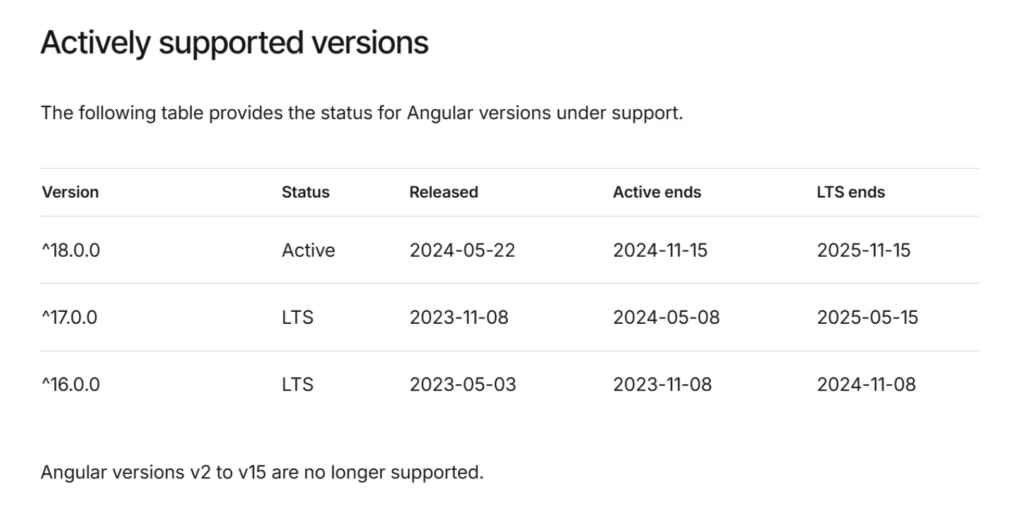
 Angular
Angular
 Third-Party Vendors
Third-Party Vendors
Sometimes, the tools and services your application relies on make changes, forcing you to adapt.
Acquisitions
A vendor or tool your application uses may get acquired, and the new owner can drastically change the product. In 2010, Oracle acquired Sun Microsystems and transformed how Java was managed. History is rife with these examples, there’s little an individual developer can do other than adapt to the changes.
Policy Changes
Platforms or distribution channels may update their policies, forcing developers to comply or risk losing support. Apple is famous for these changes, such as in 2019 when it required all apps to implement Apple sign-in to remain on the App Store.
However, some policy changes are unpopular enough to reverse, as was the case when Unity attempted to change its pricing model in 2023. After massive backlash, it reversed the policy. Not all of these policy changes are arbitrary – some come with good reason, such as WordPress’s recent ban of WP Engine.
Mistakes
Even the most reputable companies aren’t immune to errors. Case in point: in 2024, a major Crowdstrike outage disrupted millions of devices, including those at airlines like Delta, and caused significant financial damage.
Acquisitions, policy changes, and mistakes are all out of your control. No amount of planning could’ve prevented Broadcom from acquiring VMware or Apple from updating its App Store requirements. But you do have control over how quickly you react to such changes by keeping a development team up-to-date on your software and staying informed.
DDoS attacks
A Distributed Denial of Service (DDoS) attack is an unexpected spike of traffic caused by a malicious actor. This happens when an attacker (often using bots) floods your system with traffic in an attempt to take your system down or increase infrastructure costs. These attacks may come from competitors or random bad actors.
Billing alarms and regular monitoring can help you respond to these attacks quickly, limiting the impact on your budget and users. In some cases, it’s wiser to let your app go down than run up a high server bill.
Outdated Libraries
Outdated dependencies – like third-party libraries or SDKs – can bring development to a standstill. For example, Apple and Google release new versions of iOS and Android every year. While these updates aren’t an annual requirement, eventually, you’ll be forced to migrate to the latest version or risk removal from the app store. Plus, these updated SDKs often come with critical improvements. Staying proactive by updating libraries and SDKs regularly keeps your software in peak condition.
User Feedback
Good products learn from user feedback. The best products incorporate user feedback quickly and frequently. Ignoring user requests risks alienating your core user base or losing them altogether. Having a system to gather user feedback, incorporate it into your product roadmap, and communicate timelines for updates to users goes a long way in maintaining trust.
Unforeseen Events
Natural disasters, fires, or even a severed cable can take your data center offline. Without proper safeguards, you risk losing servers, data, and backups in a single incident. This is where high availability and disaster recovery plans come into play. The right team will diversify where and how your data is stored to ensure continuity no matter what happens.
Software Is a Journey, Not a Destination
Launching a software product is only the beginning. The post-launch phase is where the real work -and growth- happens. While challenges like bugs, performance issues, and security threats may arise, each obstacle serves as an opportunity to strengthen your product. With the right mindset, tools, and team, you can navigate these challenges and turn them into stepping stones to success. After all, the best software doesn’t just survive; it evolves.
Recommended for You
Check out related insights from the team
Get empowered, subscribe today
Receive industry insights, tips, and advice from Saritasa.